News
Microsoft's Tools to Fight Solorigate Attack Are Now Open Source
Microsoft open sourced homegrown tools it used to check its systems for code related to the recent massive breach of supply chains that the company has named Solorigate.
Redmond has devoted massive resources and time to address the attack on a wide variety of fronts, this week closing a comprehensive, months-long investigation after finding no evidence of access to its production services or customer data, and also no evidence that Microsoft systems were used to attack others.
It also open sourced some tools it used to check its internal systems for any signs of compromise, called CodeQL queries.
The GitHub-based project describes itself as a "semantic code analysis engine" that can help users query code as if it were data. "Write a query to find all variants of a vulnerability, eradicating it forever. Then share your query to help others do the same."
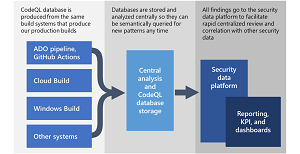 [Click on image for larger view.] CodeQL (source: Microsoft).
[Click on image for larger view.] CodeQL (source: Microsoft).
Microsoft penned a blog post yesterday in which it described CodeQL as standing out from other tools because of its two-stage approach:
First, as part of the compilation of source code into binaries, CodeQL builds a database that captures the model of the compiling code. For interpreted languages, it parses the source and builds its own abstract syntax tree model, as there is no compiler. Second, once constructed, this database can be queried repeatedly like any other database. The CodeQL language is purpose-built to enable the easy selection of complex code conditions from the database.
The post explains how the company analyzed its source code at scale in order to rule out the presence of the code-level indicators of compromise (IoCs) and Solorigate-associated coding patterns, using two different tactics. The first tactic looked for specific syntax prominent in the Solorigate code-level IoCs, such as names and particular literals. The second tactic looked for general semantic patterns for the techniques found in the code-level IoCs, particularly functionality and flow associated with the code implant. Open sourcing its tools used to fight Solorigate will help other companies conduct their own similar investigations, Microsoft said.
CodeQL was just last month featured in the GitHub Enterprise Server 3.0 Release Candidate in response to an issue calling for code scanning. "It's a developer-first, GitHub-native approach to easily find security vulnerabilities before they reach production," said GitHub, which is owned by Microsoft. "Powered by the world's most powerful code analysis engine, CodeQL, it automates security as an integral part of the developer workflow."
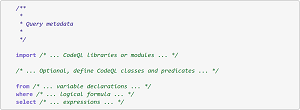 [Click on image for larger view.] Basic CodeQL Query Structure (source: Microsoft).
[Click on image for larger view.] Basic CodeQL Query Structure (source: Microsoft).
The project's Readme file titled "Working with Solorigate queries" lists many examples of specific queries used, both syntactic and semantic. For example, the syntactic queries find patterns that are above a certain threshold, with some of those patterns being "commands-in-enum" and "hashes" and "literals" and "method names." Semantic queries, meanwhile, include names like "cs/Solorigate/modified-fnv-function-detection" and "cs/backdoor/process-name-to-hash-function" and "cs/backdoor/potential-time-bomb."
Other related resources include:
About the Author
David Ramel is an editor and writer for Converge360.