News
C++ Memory Bugs Prompt Microsoft to Eye Rust Instead
Microsoft is eyeing the Rust programming language as a safer replacement of C/C++ code after discovering just how many security problems are caused by memory corruption bugs.
That news comes in a new blog post by the Microsoft Security Response Center (MSRC), which in triaging every reported Microsoft vulnerability since 2004 found that "one astonishing fact sticks out."
That astonishing fact? "The majority of vulnerabilities fixed and with a CVE [Common Vulnerabilities and Exposures] assigned are caused by developers inadvertently inserting memory corruption bugs into their C and C++ code," said Gavin Thomas, principal security engineering manager on the MSRC team, in the July 16 post titled "A proactive approach to more secure code."
While a Rust-for-C++ replacement may seem just as astonishing to some Microsoft-centric developers, Thomas said the MSRC team has a proactive role that justifies such exploration, in addition to being a response organization.
This week's post notes that Microsoft's C# and some other languages are memory-safe, in contrast to C and C++ code, whose use is causing a vulnerability problem that is only going to get worse with the use of open source code that may be riddled with memory-corruption bugs leading to security issues.
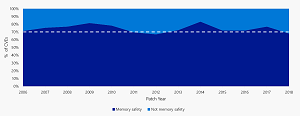 [Click on image for larger view.] Memory Vulnerabilities (source: MSRC).
[Click on image for larger view.] Memory Vulnerabilities (source: MSRC).
Thomas mentioned a presentation by MSRC team member Matt Miller at BlueHat IL earlier this year that found that "70 percent of the vulnerabilities Microsoft assigns a CVE each year continue to be memory safety issues."
Various industry sources indicate most of Microsoft's own products are written in C++, along with a lot of C, including various Windows versions, Visual Studio, Office, Internet Explorer and so on.
With the above factors in mind, the MSRC will publish further posts on the company's exploration of safer system programming languages, with Rust the initial focal point. [Update: the second post in the series was published July 18: "We Need a Safer Systems Programming Language"]
"C++ does have its virtues that make it attractive and in some cases essential: it is blisteringly fast, it has a small memory and disk footprint, it's mature, it's execution predictable, its platform applicably is almost unparalleled and you can use it without having to install additional components," Thomas said. "If only the developers could have all the memory security guarantees of languages like .NET C# combined with all the efficiencies of C++. Maybe we can: One of the most promising newer systems programming languages that satisfy those requirements is the Rust programming language originally invented by Mozilla."
By phasing out C++ code with Rust code, a whole class of vulnerabilities could be eliminated, the post suggests, lessening the burden on developers to use complicated security tools such as static analysis tools, fuzzing at scale, taint analysis and constraint solvers.
"A developer's core job is not to worry about security but to do feature work," Thomas said. "Rather than investing in more and more tools and training and vulnerability fixes, what about a development language where they can't introduce memory safety issues into their feature work in the first place? That would help both the feature developers and the security engineers -- and the customers."
Thomas mentioned
The Rust site emphasizes the language's memory safety, stating:
Rust is blazingly fast and memory-efficient: with no runtime or garbage collector, it can power performance-critical services, run on embedded devices, and easily integrate with other languages.
Rust's rich type system and ownership model guarantee memory-safety and thread-safety -- and enable you to eliminate many classes of bugs at compile-time.
Rust was identified as the "most loved" programming language in Stack Overflow's huge developer survey earlier this year.
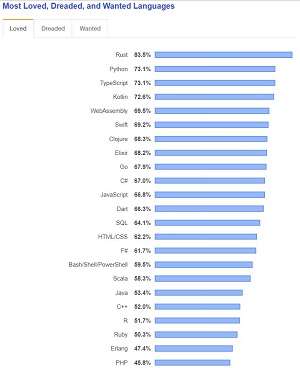 [Click on image for larger view.] Whole Lotta Rust Love (source: Stack Overflow).
[Click on image for larger view.] Whole Lotta Rust Love (source: Stack Overflow).
Mozilla, the creator of Rust, said it was created in 2006 as "an alternative to C/C++," listing its distinguished features as:
- zero-cost abstractions
- move semantics
- guaranteed memory safety
- threads without data races
- trait-based generics
- pattern matching
- type inference
- minimal runtime
- efficient C bindings
The MSRC post prompted a plethora of "pingbacks" and an expression of support from one developer who said: "That is awesome! I hope the Rust efforts move forward. It is a wonderful language, and a necessary step forward."
About the Author
David Ramel is an editor and writer at Converge 360.