News
North Korea-Sponsored Hackers Attack with Bad-Code Visual Studio Projects
Microsoft reported a battle with North Korean-sponsored hackers who attacked security researchers with a most innovative technique: compromised Visual Studio projects.
The attack was attributed to a group called ZINC, said to be associated with the Democratic People's Republic of Korea (DPRK).
A Jan. 28 post titled "ZINC attacks against security researchers" described the organization as a DPRK-affiliated and state-sponsored group. That determination was based on "observed tradecraft, infrastructure, malware patterns, and account affiliations."
"This ongoing campaign was reported by Google’s Threat Analysis Group (TAG) earlier this week, capturing the browser-facing impact of this attack," Microsoft said. "By sharing additional details of the attack, we hope to raise awareness in the cybersecurity community about additional techniques used in this campaign and serve as a reminder to security professionals that they are high-value targets for attackers."
While such battles between hackers and enterprises and security organizations are obviously common and ongoing, one unusual aspect of this encounter was the choice of payloads for the bad code.
"ZINC used a variety of new techniques to target the victims, including gaining credibility on social media with genuine content, sending malicious Visual Studio projects, and using a watering hole website weaponized with browser exploits."
The contaminated VS projects contained prebuilt binaries, including a malicious DLL (dynamic link library) that masqueraded as a database file. The idea was to trick users into launching the projects and tripping attack code.
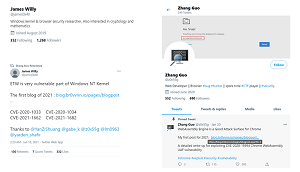 [Click on image for larger view.] Actor-Controlled Twitter Handles (source: Microsoft).
[Click on image for larger view.] Actor-Controlled Twitter Handles (source: Microsoft).
The Google post provided more information on the slick use of social media:
The actors have been observed targeting specific security researchers by a novel social engineering method. After establishing initial communications, the actors would ask the targeted researcher if they wanted to collaborate on vulnerability research together, and then provide the researcher with a Visual Studio Project. Within the Visual Studio Project would be source code for exploiting the vulnerability, as well as an additional DLL that would be executed through Visual Studio Build Events. The DLL is custom malware that would immediately begin communicating with actor-controlled C2 domains.
Microsoft security pros said the company's Defender for Endpoint tool detects the bad DLLs as Comebacker malware. "A pre-build event with a PowerShell command was used to launch Comebacker via rundll32. This use of a malicious pre-build event is an innovative technique to gain execution."
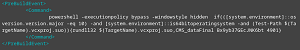 [Click on image for larger view.] Visual Studio Build Events Command Executed when Building the Provided VS Project Files (source: Google).
[Click on image for larger view.] Visual Studio Build Events Command Executed when Building the Provided VS Project Files (source: Google).
The complicated attacks also used a variety of other techniques, including:
- Klackring malware: "Klackring is a DLL that registers a malicious service on the targeted machine."
- MHTML file: "ZINC sent researchers a copy of a br0vvnn blog page saved as an MHTML file with instructions to open it with Internet Explorer. The MHTML file contained some obfuscated JavaScript that called out to a ZINC-controlled domain for further JavaScript to execute."
- Driver abuse: A buggy attempt to use an old driver to exploit a known vulnerability.
- Other malware: These included an encrypted Chrome password-stealer.
- C2 communication: "After establishing a command-and-control (C2) channel on a targeted device, the backdoor is configured to check into the C2 servers every 60 seconds. Over this C2 channel, the threat actors can execute remote commands to enumerate files/directories and running processes, and to collect/upload information about the target device, including IP address, Computer Name, and NetBIOS."
Microsoft pointed to several tools and techniques organizations can use to improve their security posture against such attacks, including measures to take if a specific ZINC-owned blog was visited with a Chrome browser, which could transmit the malware. Researchers also detailed measures to take going forward: "For proactive prevention of this type of attack, it is recommended that security professionals use an isolated environment (e.g., a virtual machine) for building untrusted projects in Visual Studio or opening any links or files sent by unknown parties."
Much more detailed information can be found in the Microsoft and Google posts, including a list of "indicators of compromise" on the former and a list of known actor-controls sites and accounts in the latter. Neither one reported any specific damage from ZINC.
Note that this wasn't Microsoft's first run-in with ZINC (aka the Lazarus Group), as the company teamed up with Facebook to battle the group three years ago.
About the Author
David Ramel is an editor and writer at Converge 360.