News
VS Code's 'Workspace Trust' Can Restrict Automatic Code Execution
After the Visual Studio Code dev team introduced Workspace Trust in last month's regular update, it recently published guidance to explain the reasoning behind giving users the option to restrict automatic code execution in the open source-based, cross-platform code editor.
While explaining that reasoning, the team also noted that Workspace Trust is a work in progress, with improvements coming in the next update, v1.58.
The June 2021 v1.57 update, meanwhile, provided the initial introduction, building upon previous Workspace Trust functionality for extensions. Now, once enabled, this feature pops up a dialog asking "Do you trust the authors of the files in this folder?" when a folder/workspace is opened up. Microsoft last month said, "This dialog is important for allowing the user to make a decision early and understand the impact of their decision. Once you understand the feature, you may want to customize when to display the dialog using the security.workspace.trust.startupPrompt setting."
In a blog post published this week, Microsoft's Chris Dias detailed the history of the feature and why it was introduced.
They "why" is to prevent security risks associated with unintended code execution when a user opens a workspace in VS Code. Possibly bad (security-wise) code can be executed without a user necessarily wanting to do so. Developers may be aware of the risks in firing off such code while doing automated testing or debugging, or running npm install or make, or building a Java or C# project.
However, Dias said less obvious code execution could happen with a linter or other tools/scenarios, such as:
- The
preLaunchTask that runs before starting the app and can run a build that has an extra task executing arbitrary code unrelated to the build
- An npm module could steal crypto wallet private keys
- When making a simple edit, a malicious linter is loaded from the node_modules folder, instead of the one that is installed globally
- Even reading code can be deceptive, because attackers can use Unicode hacks to hide malicious code in plain sight
After trying different security schemes that resulted in a string of whack-a-mole remediations of continually exposed vulnerabilities via multiple prompts, or "notification fatigue" or other issues, the Workspace Trust concept was chosen, prompting users to trust files or folders when they are first opened, while allowing them to customize how the feature works.
According to this graphic (apparently from social media) in this week's post, some developer feedback on earlier iterations of the feature wasn't exactly positive:
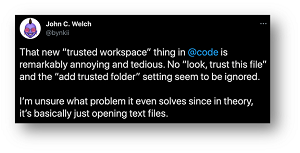 [Click on image for larger view.] Workspace Trust Complaint (source: Microsoft).
[Click on image for larger view.] Workspace Trust Complaint (source: Microsoft).
"The decision to trust a folder has a fundamental impact on the capabilities of VS Code, so after all the research we decided the right thing was to ask the trust question right away when you try to open a folder," Dias said. "Because the modal dialog is disruptive, we try to balance things out by making the dialog powerful so that you could answer a couple of questions and in the end, see the prompt much less often in your day-to-day work.
"From our own dogfooding as well as through interviews with other developers, we found that people generally have a primary folder where they put all their sources and consider it trustworthy. We therefore added the ability to trust the parent folder directly from the dialog. You can trust it and all the sub folders with one click and then you won't see the trust prompt again."
Thus, upon opening a folder, this prompt is displayed:
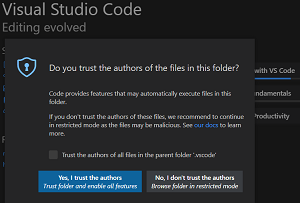 [Click on image for larger view.] Prompt Opening a Folder
[Click on image for larger view.] Prompt Opening a Folder
Upon opening "untrusted" files in a folder that has already been trusted, this prompt is displayed:
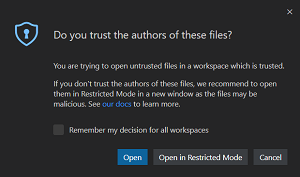 [Click on image for larger view.] Prompt Opening a File
[Click on image for larger view.] Prompt Opening a File
The Workspace Trust editor informs the user that in a trusted folder:
- Tasks are allowed to run
- Debugging is enabled
- All workspace settings are applied
- All extensions are enabled
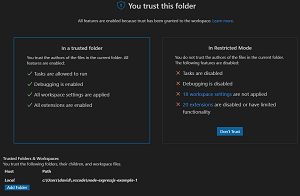 [Click on image for larger view.] You Trust This Folder
[Click on image for larger view.] You Trust This Folder
If the user doesn't trust the folder, the user is informed that Restricted Mode is enacted, prohibiting all of the above actions:
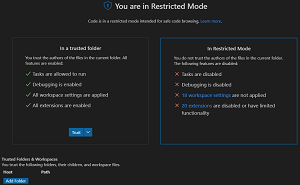 [Click on image for larger view.] You Are in Restricted Mode
[Click on image for larger view.] You Are in Restricted Mode
As noted, many actions are available right from the Workspace Trust editor:
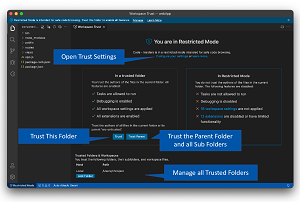 [Click on image for larger view.] Workspace Trust Editor Actions (source: Microsoft).
[Click on image for larger view.] Workspace Trust Editor Actions (source: Microsoft).
and customization is available in the settings:
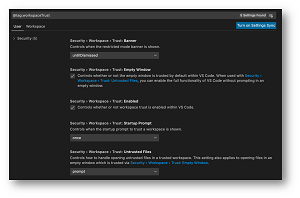 [Click on image for larger view.] Workspace Trust Customization (source: Microsoft).
[Click on image for larger view.] Workspace Trust Customization (source: Microsoft).
For the next update, v1.58, more Workspace Trust functionality is planned, and the roadmap's security work includes: "Trusted workspaces: Ensure it's safe to clone a repo and read the source code without any unauthorized code execution."
Much of the work will affect extensions, as a main 2021 theme for VS Code is to explore signed and sandboxed extensions, along with introducing Workspace Trust.
"Looking ahead, we want to help extension authors avoid arbitrary code execution and provide more functionality when running in Restricted Mode," Dias said. "Our Roadmap notes the work we are doing with the Visual Studio Marketplace team to bring additional security to the extension ecosystem (we call this 'Trusted Extensions'), including validated publishers, signing and platform-specific extensions. In short, you can think of Workspace Trust as helping good extensions make good decisions. Trusted Extensions will help protect you from bad extensions."
About the Author
David Ramel is an editor and writer at Converge 360.