News
Microsoft Secures Visual Studio Live Share Sessions
Microsoft has enhanced the security of Visual Studio Live Share, its real-time collaborative development tool.
Live Share, as its name suggest, helps developers collaboratively edit and debug with others using any programming language or app type. Participants can securely share a current project, jointly debug, share terminal instances, forward localhost web apps, conduct voice calls and more. It differs from similar approaches like pair programming in that it lets developers work together while still retaining their personal editor preferences such as themes and keybindings -- while also controlling their own cursor.
However, just like Microsoft Teams and other collaboration tools, opening up enterprise systems to people all over the world is fraught with potential security issues. It already has many baked-in security features, but Microsoft last week highlighted some recent enhancements.
 [Click on image for larger, animated GIF view.] Visual Studio Live Share in Animated Action (source: Microsoft).
[Click on image for larger, animated GIF view.] Visual Studio Live Share in Animated Action (source: Microsoft).
"Whether you're looking to restrict access to only individuals in your organization or to disable read-write terminals, your organization can now configure policies for proper control and compliance," said Microsoft's Carolina Uribe-Gosselin, product manager, in an Aug. 17 blog post.
In announcing new enterprise polices for Live Share, Uribe-Gosselin said the dev team was responding to feedback from developers who would like to use it but can't because it lacks controls to let organizations prevent people from outside a domain from joining Live Share sessions.
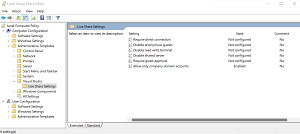 [Click on image for larger view.] Visual Studio Live Share Group Policy Editor (source: Microsoft).
[Click on image for larger view.] Visual Studio Live Share Group Policy Editor (source: Microsoft).
That concern, among many others, is addressed in these policies:
- Allow only company domain accounts: Prevents users from being able to share their session with any guests who are not part of the domain that the organization allows via policy. Users must also be logged in with the domain account that the organization allows via this policy to share a session. When enabling this policy, multiple domains can be added by using a semicolon to separate each domain.
- Disable read-write terminals: Prevent the host from being able to explicitly share a new writeable terminal. This policy also suppresses the option for the guest to request write access to a terminal. This would effectively look like the experience you see today in a read-only session (you can't share writeable terminals) but would apply to read/write sessions too.
- Disable shared servers: Prevent the host from being able to explicitly share a new server, as well as auto-sharing of servers from the terminal. In this mode, the "Shared Servers" node in the "Session Details" tree view will be hidden, along with all associated commands.
- Require direct connection: Prevents hosts from allowing relay-based guests from joining their session. Organizations might want to configure this policy, so guests connect directly to the host without going through the web. Live Share already supports the "Live Share: Connection Mode" setting, and so this policy is effectively just enforcing it to "direct."
- Disable anonymous guests: Disallow anonymous guests from joining a session. We already have the "Live Share: Anonymous Guest Approval" setting, and so this policy is effectively just enforcing that to "reject."
- Enforce accepting/rejecting a guest: Requires the host to individually accept each guest that attempts to join a session.
Live Share 2022 is available from the Visual Studio Marketplace.
About the Author
David Ramel is an editor and writer at Converge 360.