News
Electron-Based App Vulnerabilities Hit VS Code, Microsoft Teams
A team of researchers recently presented data about vulnerabilities in apps built on the open source Electron framework for creating desktop apps with JavaScript, HTML and CSS.
In that camp are Visual Studio Code and Microsoft Teams.
Featuring a team of security experts from Electrovolt, which does code reviews, penetration testing and design review consulting, the presentation was titled Pwning Popular Desktop apps while uncovering new attack surface on Electron.
And pwn they did, achieving remote code execution (RCE) -- wherein an attacker remotely executes commands on a victim's computing device -- on 20 Electron-based applications. In addition to VS Code and Microsoft Teams, that list includes Discord, JupyterLab, Mattermost, Rocket.Chat, Notion, BaseCamp and many others.
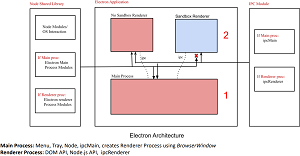 [Click on image for larger view.] Electron Architecture (source: Electrovolt/Black Hat).
[Click on image for larger view.] Electron Architecture (source: Electrovolt/Black Hat).
The team offered three takeaways from the research, which involved achieving RCE by getting users to click on links sent to them within the applications:
- Electron apps are Ideal adversarial (or red team) target as users will click anywhere or open messages.
- Dig deeper into the framework you're auditing and don't limit yourself to only the application layer
- Minimize attack surface on the apps as much as possible. (Open URL redirect can also be turned into RCE some day)
Over the past few months, the team has posted blog posts on several of the investigations, including one titled Visual Studio Code - Remote Code Execution in Restricted Mode (CVE-2021-43908).
"We all know, VSCode is one of the most used Electron App. As a part of our research on hacking electron apps, we thought it would be cool to pwn VSCode and we were able to pwn it. We were able to achieve RCE on VSCode without getting to use any of our new fancy stuff," the post said, appending this TL;DR: "Remote Code execution can be achieved when a victim opens a markdown file in a maliciously crafted VSCode Project or a folder even in VSCode Restricted Mode."
The fix for the associated CVE (Common Vulnerabilities and Exposures) item No. 2021 43908 ("Visual Studio Code Spoofing Vulnerability"), was actually released last December, leading to a corresponding $3,000 bug bounty payout from Microsoft Security Response Center.
There was no blog post for the Microsoft Teams vulnerability, which also paid a $3,000 bounty and had something to do with reading local files.
To protect against vulnerabilities that haven't been patched, the team offered the following mitigations:
- Enable all the security flags
- Don't use embeds which don't have good security track record (third party embed)
- Mitigate security vulnerabilities (XSS, Open URL Redirection, etc.) on all your assets (even subdomains)
- Upgrade Electron regularly to make sure patch gap is not large
- Don't implement sensitive IPC on main process
- Ensure that all IPC message handlers appropriately validate senderFrame
- Ensure Adequate Segregation is present if you're rolling out your own library which combines browser and application-level code
Interestingly, the presentation included much discussion about renderers and sandboxes, and this month's release of Electron 20.0.0 included this new feature: "Renderers are now sandboxed by default unless nodeIntegration: true or sandbox: false is specified."
Electrovolt researchers participating in the project were Mohan Sri Rama Krishna, Max Garrett, Aaditya Purani and William Bowling.
About the Author
David Ramel is an editor and writer at Converge 360.