News
Security Report: Remote Code Execution Is Top .NET Threat Type
Snyk, an open source security specialist, published a new report on .NET security, finding that remote code execution, cross-site scripting and denial-of-service vulnerabilities account for two-thirds of the known vulnerabilities in the .NET ecosystem.
The company scanned thousands of .NET projects finding direct and indirect dependencies that can introduce vulnerabilities, noting that the average project has about 11 direct dependencies and 76 indirect dependencies, so vulnerabilities can often be introduced via multiple paths.
In the bad new/good news department, Snyk said that although a large percentage of the vulnerabilities are of high severity, they all can be fixed. "All of the known vulnerabilities found in the .NET ecosystem have available remediation, meaning that once our users knew of the security vulnerabilities, there were steps they could take to secure their project," the company's .NET open source security insights post states.
Another post details the libraries associated with the most common vulnerabilities, a list headed by: system.net.http, system.io.pipelines, microsoft.aspnetcore.server.kestrel.core and so on.
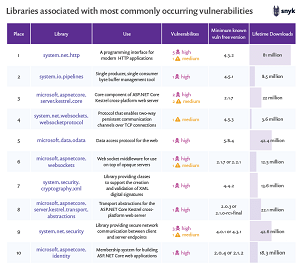 [Click on image for larger view.] Libraries Associated with the Most Common .NET Vulnerabilities (source: Snyk).
[Click on image for larger view.] Libraries Associated with the Most Common .NET Vulnerabilities (source: Snyk).
"When reviewing this table, a few things stand out," the second post said. "First, the ASP.NET Core Kestrel cross-platform web server is both popular, and has seen a number of high severity vulnerabilities derived from several different related libraries.
"Second, the total number of vulnerabilities for these libraries is generally low, but the severities are generally high."
Yet a third post about the report finds that remote code execution, cross-site scripting, and denial-of-service vulnerabilities are the most common vulnerabilities, accounting for some two-thirds of those known.
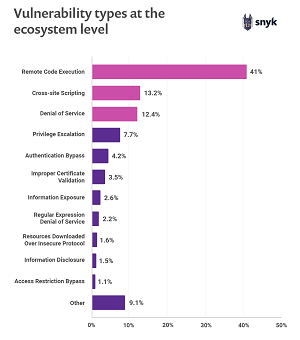 [Click on image for larger view.] Vulnerability Types at the Ecosystem Level (source: Snyk).
[Click on image for larger view.] Vulnerability Types at the Ecosystem Level (source: Snyk).
Other takeaways from the report include:
- NuGet stats: 150,000-plus unique packages; 1.6 million package versions; 20 billion total downloads; 26 percent increase in packages between 2018 and 2019
- 71 percent of vulnerabilities are rated as high severity
- An average project has 5 unique high severity vulnerabilities, 2 unique medium
severity vulnerabilities, and 1 unique low severity vulnerability
"In the .NET ecosystem, the number of vulnerabilities per package is low, but the severity of those vulnerabilities tends to be high," Snyk concluded. "This means less time is likely needed to resolve the problems (lower investment) but you are addressing potentially dangerous security problems (high return). In other words, by addressing known vulnerabilities in the .NET packages that you use, you are taking a security step that has a high return on investment."
About the Author
David Ramel is an editor and writer at Converge 360.