News
Attacks on .NET Apps Grow in Number, Severity, Says Security Firm
.NET apps were found to have more serious vulnerabilities and suffer more attacks last year, according to data gathered by Contrast Labs.
The firm publishes vulnerability and attack metrics on a bimonthly basis in order to provide actionable data for organizations. It also just published its "2020 Application Security Observability Report," which analyzed application security (AppSec) trends for the 12 months ending on May 31, 2020.
.NET Is Bigger Target
Some interesting .NET metrics come from the September–October 2020 time frame. Here's what the report announcement had to say after noting that .NET applications had more serious vulnerabilities in that period, while experiencing more attacks:
"Serious Cross-site Scripting and Broken Access Control vulnerabilities were found in 2 percent more applications in September–October compared to July–August (representing a 23 percent and 31 percent increase, respectively). Cross-site Scripting vulnerabilities provide an opportunity for bad actors to masquerade as a 'victim user' in order to carry out any actions that the user is able to perform and access any of the user's data. Broken Access Control vulnerabilities allow attackers to bypass authorization safeguards and perform tasks as if they were privileged users. Both Cross-site Scripting and Broken Access Control vulnerabilities, if exploited, can enable bad actors to access and control an application's functionality and data.
"These two vulnerabilities drove the increased prevalence of serious vulnerabilities within .NET applications in September–October. Specifically, Cross-site Scripting vulnerabilities were identified in 12 percent of .NET applications and serious Broken Access Control vulnerabilities were identified in 7 percent of .NET applications."
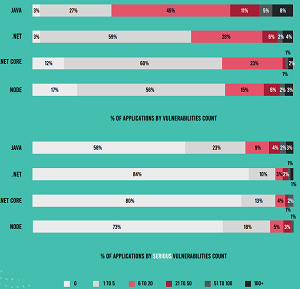 [Click on image for larger view.] Percent of Applications by Number of Reported Vulnerabilities and Serious Vulnerabilities, by Application Language. (source: Contrast Labs).
[Click on image for larger view.] Percent of Applications by Number of Reported Vulnerabilities and Serious Vulnerabilities, by Application Language. (source: Contrast Labs).
As far as the increased rate of attacks, the biggest change came from more Command Injection attacks, with 98 percent of applications targeted in September–October, up from 57 percent in July–August. On the positive side, Cross-site Scripting saw a smaller increase in attacks, while Broken Access Control vulnerabilities accounted for fewer attacks.
.NET vs. Java
The report also contrasted the difference in attacks on .NET vs. Java apps, finding the latter present more security issues.
"Notably, twice as many Java applications have at least one serious vulnerability than .NET ones," the report said. "Specifically, over twice as many Java applications have at least one serious vulnerability compared to .NET and .NET Core -- 42 percent versus 16 percent and 20 percent, respectively. And 18 percent of Java applications have at least six serious vulnerabilities, while only 7 percent of .NET ones have that many. Particular problem areas for Java applications include broken access control (26 percent) and XSS (22 percent). This can be traced to a lack of standardization in Java, which is an open-source language -- compared with .NET, which is highly standardized and controlled by Microsoft."
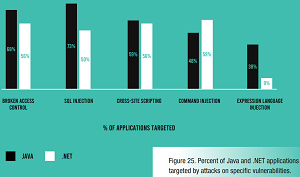 [Click on image for larger view.] Percent of Java and .NET Applications Targeted by Attacks on Specific Vulnerabilities (source: Contrast Labs).
[Click on image for larger view.] Percent of Java and .NET Applications Targeted by Attacks on Specific Vulnerabilities (source: Contrast Labs).
Furthermore, in more discussion about security problems with open source libraries, the report said, "The top Common Vulnerabilities and Exposures (CVEs) for software written in Java have significantly higher Common Vulnerability Scoring System (CVSS) scores than the CVSS scores for the top .NET CVEs, suggesting higher risk for Java applications."
Other Highlights
Other key findings as highlighed by Conrast include:
- Vulnerabilities: Nearly all applications have at least one vulnerability, and more than one-quarter have a serious one. 11 percent of applications have more than six serious vulnerabilities. Well over half of applications have insecure configuration and sensitive data exposure vulnerabilities.
- Attacks: On average, each application endured more than 13,000 attacks per month in the past year, with injection, cross-site scripting, and broken access control topping the attack-vector list. Fortunately, 98 percent of attacks do not hit an existing vulnerability. The high volume of attempts to infiltrate applications accentuates the need to effectively prioritize remediations and take steps to block attacks on applications in production. Organizations can protect themselves by taking a strategic, risk management-based approach to application security. This means prioritizing vulnerabilities according to the risk they pose, which requires organizations to have actionable data not only at an industry level but also for the specific organization.
For much more data, including recommendations from Contrast, see this post, from which the report can be accessed.
About the Author
David Ramel is an editor and writer at Converge 360.