News
.NET Apps Show Poorly in Software Security Report
Veracode's new software security report found .NET applications had the highest percentage of flaws when compared to two popular programming languages (even though .NET isn't a programming language).
The latest edition of the application security specialist's annual report series -- State of Software Security 2023 -- examined .NET, JavaScript and Java. (A friendly reminder to Veracode: .NET is a framework, not a language; this issue dates back to 2013.)
One part of the huge, stats-heavy report examined existing flaws in applications by language, where .NET topped the charts, in a bad way. As seen in the figure below, .NET apps had the highest percentage of "Any Flaws" and "OWASP Top 10" flaws and "High Severity" flaws:
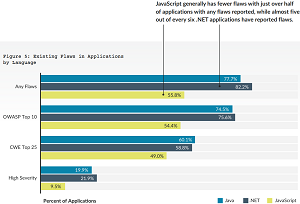 [Click on image for larger view.] Existing Flaws in Applications by Language (source: Veracode).
[Click on image for larger view.] Existing Flaws in Applications by Language (source: Veracode).
"JavaScript generally has fewer flaws with just over half of applications with any flaws reported, while almost five out of every six .NET applications have reported flaws," the report said.
As far as what flaws were found in .NET, another chart showed CWE-829 -- inclusion of Functionality from Untrusted Control Sphere -- was the most prevalent, found in 90.3 percent of applications.
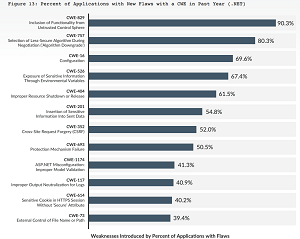 [Click on image for larger view.] Percent of Applications with New Flaws with a CWE in Past Year (.NET) (source: Veracode).
[Click on image for larger view.] Percent of Applications with New Flaws with a CWE in Past Year (.NET) (source: Veracode).
The report contains findings about applications that were subjected to static analysis, dynamic analysis, software composition analysis and/or manual penetration testing via the company's cloud-based platform.
A .NET-specific section provides details about the framework's apps while also indicating what types of statistics are included in the sprawling, 64-page report PDF:
We turn our attention to .NET and see a slightly different picture as compared to the other languages. 51 percent of .NET applications are reducing tech debt, which means application developer teams seem to be getting slightly more than half the flaws — faster than other languages in this data (with the oft-recurring exception of JavaScript).
When you look at these bars in Figure 11, what at first you might have thought is only a slightly more aggressive remediation percentage rate translates into differences in the remediation curve that you can begin to count in your head. You can see this in the time to close half the flaws as.NET pulls away from Java by close to 100 days. That's encouraging news for .NET, and a peek at the remediation curve (way back up in Figure 7) shows that at the two-year mark about one in five flaws are still open in.NET. Java comes in at just over one in four. Then with the remediation curve in mind, if you compare Figure 12 versus Figure 9 it is clear that a slightly more aggressive remediation percentage translates into reduced chances that something is still open. Overall it is a second place sweep for .NET.
This chart illustrates that second-place sweep:
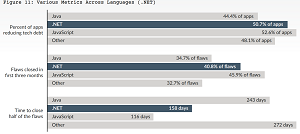 [Click on image for larger view.] Various Metrics Across Languages (.NET) (source: Veracode).
[Click on image for larger view.] Various Metrics Across Languages (.NET) (source: Veracode).
Speaking to that, the report said: "The problem here can be the severity of flaws that are introduced and the time it takes to fix them. As mentioned previously in the Java section, each language seems to have its own predisposition to high- and critical-severity flaws that then wind up appearing in large numbers."
Veracode said its research this year centered on a crucial question: what can be done to avoid introducing security flaws in the first place?
It also listed the three main takeaways from the entire report, which was topped by the tagline: "An Ounce of Prevention is Worth a Pound of Cure":
- 32 percent of apps contain security flaws at the first scan, and by the five-year mark, this jumps to 70 percent.
- Certain choices made early in development can measurably improve security posture in the long run.
- Open source may be extremely fragile, so proceed with caution.
That last point has been echoed in several other studies, including last year's Veracode report (see the Virtualization & Cloud Review article, "App Security Report: Open Source Code Still 'Blessing and a Curse'." The open source problem has been recognized for years (see the 2017 Application Development Trends article, "Study Examines Open Source Risks in Enterprise Software") and has continued (see last year's article, "Report: Open Source Security Ignored by Many Organizations").
To address issues found in the report, Veracode advised organizations to steepen the remediation curve, because applications accumulate flaws by the time they're two years old. "It is clear that something happens to the application or to the groups developing them," the company said. "Whether increasing application complexity from years of steady growth or diminishing focus on production applications over time, this familiar pattern of an upwards slant is clear to see. We do know that by the time an application is 10 years old there is a 90 percent chance that it has at least one flaw."
It also advised they prioritize automation and developer training, along with establishing application lifecycle management.
"Tackling technical debt by remediating security flaws as early and quickly as possible can save teams major headaches -- and hefty 'interest' payments in the form of the time it takes to remediate accumulated flaws -- down the road," Veracode said. "Thankfully, there are data-driven, concrete steps teams can take to help meet this objective, including increasing scan cadence, scanning via API, and implementing developer education."
About the Author
David Ramel is an editor and writer at Converge 360.